What is Bcrypt? A Complete Guide to Modern Password Hashing
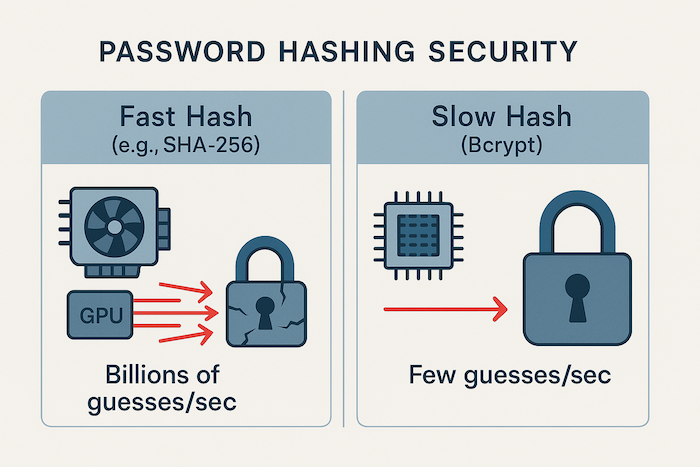
Simply hashing a password with a quick technique like SHA-256 is insufficient in the realm of password security. Because modern GPUs can guess billions of hashes per second, brute-force assaults can be used to break rapid hashes. Specialized password hashing functions are useful in this situation. Bcrypt is a well-known, tried-and-true algorithm created especially to secure passwords. Because it is purposefully slow, flexible, and automatically adds salt, developers all over the world choose it. We'll go into great detail about what bcrypt is, why it's so safe, and how it stacks up against other techniques in this guide.
Why Do We Need a Special Function Like Bcrypt?
We must first comprehend the issue that bcrypt addresses—the weakness of rapid hashes—in order to appreciate its significance.
The main goal of algorithms such as MD5 and SHA-256 is speed. They are designed to swiftly calculate a hash from a huge message or file. For jobs like confirming file integrity, this is great. But when it comes to password storage, this quickness turns into a serious flaw.
A hacker with access to a password hash database can execute "brute-force" or "dictionary" assaults using contemporary hardware, such as Graphics Processing Units (GPUs). These GPUs can test billions of popular passwords every second against a single stolen hash because a rapid hash can be computed in a fraction of a second. A password that is "password123" will probably be cracked relatively immediately. At this point, a deliberate, slow algorithm is crucial.
So, What is Bcrypt?
A powerful and thoroughly tested encryption technique, the Blowfish cipher, serves as the foundation for the password-hashing feature Bcrypt. It was created by Niels Provos and David Mazières with the express purpose of being sluggish and impervious to attacks that were accelerated by hardware. It was originally demonstrated at USENIX in 1999.
Unlike general-purpose hash functions, bcrypt has two key features built directly into its design:
- It's Adaptive and Slow: Bcrypt's most important feature is its configurable "cost factor" (also known as "work factor" or "log rounds"). A developer can purposefully slow down the hashing process using this parameter. You may "tune" the slowness by increasing the cost factor, which keeps brute-force attacks computationally costly for an attacker even as computers and GPUs get faster over time. The long-term resilience of bcrypt is attributed to this adaptability.
- It Includes a Salt Automatically: Bcrypt automatically generates a random salt for each password before hashing it. A special string of information that is mixed with the password is called a salt. This implies that two users' stored hashes will differ greatly, even if they have the same password. The "rainbow table" assaults, which use lists of hashes for popular passwords that have already been calculated, are defeated by this method alone. Internally, Bcrypt manages this salting procedure, guaranteeing its accuracy and security.
How to Use Bcrypt: Practical Examples
The intricacy of creating salts and comparing hashes is taken care of for you by the well-supported, user-friendly libraries for bcrypt found in the majority of contemporary programming languages. Here are a few typical instances.
Bcrypt in Python
First, you'll need to install the library using pip:
pip install bcryptThen, you can use it in your code:
import bcrypt
password = b"a_very_secure_password"
# To hash a password for the first time
# The salt is automatically generated and included in the hash
hashed = bcrypt.hashpw(password, bcrypt.gensalt())
print(hashed)
# Example output: b'$2b$12$Ea.Kj9.Sj0iYyZ.9.v.8.u1b5z0b9g5w8d7e6f4a3c2b1a0'
# To check a password against a stored hash
if bcrypt.checkpw(password, hashed):
print("Login successful")
else:
print("Invalid password")Bcrypt in Node.js (JavaScript)
The most popular library in the Node.js ecosystem is `bcrypt` (or `bcryptjs` for a pure JavaScript implementation). Install it with npm:
npm install bcryptAnd use it in your application:
const bcrypt = require('bcrypt');
const password = "a_very_secure_password";
const saltRounds = 10; // This is the cost factor
// To hash a password
bcrypt.hash(password, saltRounds, function(err, hash) {
if (err) {
// Handle error
return;
}
console.log(hash);
// Example output: '$2b$10$fL6fH7o.x.p2b.r/r/R5bOcL3.O/3g4i2j1h0'
// To check a password
bcrypt.compare(password, hash, function(err, result) {
if (result === true) {
console.log("Login successful");
} else {
console.log("Invalid password");
}
});
});Bcrypt vs. SHA-256: Which is Better for Passwords?
For any developer, this is an important distinction. Although they are both hashing algorithms, their purposes are distinct. Compared to a basic SHA-256 hash, Bcrypt is far superior and more safe for password hashing. If you need a refresher on the basics, check out our complete guide to hashing.
| Feature | Bcrypt | SHA-256 (for passwords) |
|---|---|---|
| Designed For | Password Hashing (Slow) | General Hashing (Fast) |
| Salting | Automatic & built-in | Manual implementation required |
| Adaptability | Adjustable "cost factor" | Fixed speed |
| Recommendation | Excellent for passwords | Not Recommended for passwords |
When NOT to Use Bcrypt
While Bcrypt is a top-tier choice for password hashing, it's the wrong tool for other jobs. Its deliberate slowness makes it unsuitable for tasks that require high performance, such as:
- File Integrity Checks: You wouldn't want to wait several seconds to generate a hash for a large file. For this, a fast algorithm like SHA-256 is the correct choice.
- Database Lookups (Hash Tables): The speed of a hash function is critical for the performance of hash tables. Using bcrypt here would cripple database performance.
- Unique Identifiers: When you need a quick, non-secure hash to use as an identifier (e.g., for a cache key), bcrypt is overkill and too slow.
Answering Common Questions about Bcrypt's Security
Is bcrypt secure?
Yes. Bcrypt is still regarded as a very safe, dependable, and strong option for password hashing as of 2025. When used properly, its architecture has withstood the test of more than 20 years and is still very resilient to the most prevalent password attack types.
Can bcrypt be reversed, decoded, or decrypted?
No. This is a typical misunderstanding. Bcrypt is a one-way function, just like any other appropriate cryptographic hash function. A bcrypt hash cannot be mathematically reversed to yield the original password due to computational limitations. Instead of truly reversing the technique, websites that make claims to "decrypt bcrypt" use extensive databases of known password-hash pairs (from prior data breaches) to see if your hash is included. Your password must be unique for these services to work.
What are the weaknesses or disadvantages of bcrypt?
While very strong, bcrypt is not perfect. Its known limitations include:
- Password Length Limitation: Passwords are truncated at 72 characters by the original bcrypt method. This is a technical limitation of the algorithm, although it is not a practical problem for almost all user passwords.
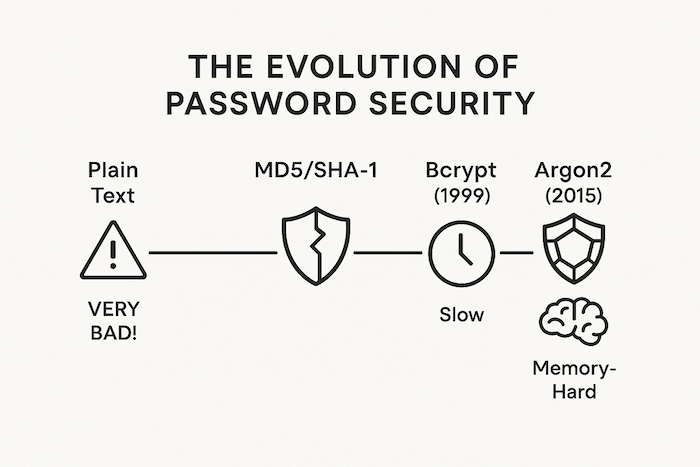
- Not "Memory-Hard": Bcrypt is not as "memory-hard" as more recent algorithms, but it is "CPU-hard" (requiring a lot of processing power). This implies that rather than using memory-hard methods like Argon2, specialized, costly technology (like ASICs) can be made to accelerate the cracking of bcrypt.
Is there anything better than bcrypt? Is bcrypt still relevant?
Yes, newer algorithms are deemed "better" from a technological standpoint. The current winner of the official Password Hashing Competition is Argon2. Argon2 is both CPU- and memory-hard, making it more resistant to custom hardware attacks.
However, bcrypt is still absolutely relevant and a very safe option. It has been battle-tested for more than 20 years, is widely used in all major programming languages, and is well-known in the security world. For the great majority of applications, using bcrypt is never a bad security choice. It offers good protection.
Understanding the Bcrypt Hash String
A common question is what the different parts of a bcrypt hash mean. A typical bcrypt hash looks like this:
$2b$12$AbCdEfGhIjKlMnOpQrStUuVwXyZaBcDeFgHiJkLmNoPqRsTLet's break it down:
$2b$: This identifies the bcrypt algorithm version.12$: This is the cost factor (in this case, 212 rounds of hashing).AbCdEfGhIjKlMnOpQrStUu: This is the 22-character salt that was randomly generated and is stored as part of the hash.VwXyZaBcDeFgHiJkLmNoPqRsT: This is the actual computed hash of the password and salt.
When you use a function like `bcrypt.checkpw()`, the library knows how to parse this string, extract the salt and cost factor, and apply them to the password you're trying to verify.
Bcrypt: A Timeless Choice for Password Security
To summarize, bcrypt's deliberate slowness and its built-in, automated salting make it a powerful and reliable choice for protecting user passwords. It directly counters the threat of fast, hardware-accelerated brute-force attacks. While newer alternatives like Argon2 offer additional technical advantages, bcrypt's long and proven history of security, combined with its wide adoption and support, make it a trusted and highly recommended standard for any developer who is serious about protecting user data.