What is Hashing? A Comprehensive Guide for Beginners
Imagine you have a secret message, and you want a way to create a unique, fixed-length "fingerprint" for it. This fingerprint would change drastically even if you altered just one letter of your message, but it would always be the same if the message stayed identical. This, in essence, is what hashing is all about. Hashing is a fundamental concept in computer science and cybersecurity, used to ensure data integrity, secure passwords, and much more. In this guide, we'll explore what hashing is in simple terms, how it works, and why it's so crucial in the digital world.
What is Hashing in Simple Terms?
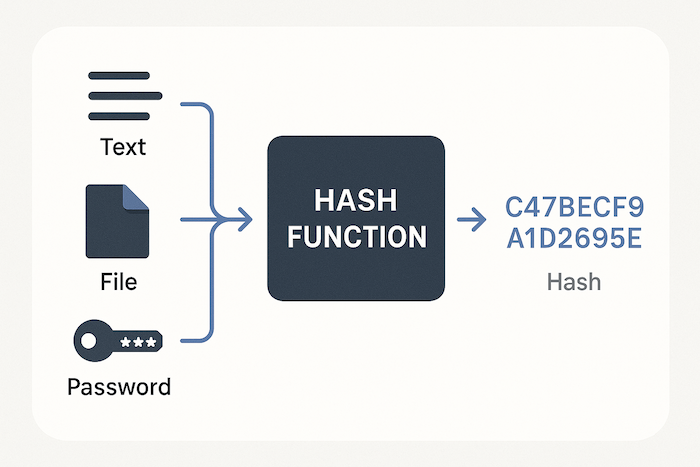
At its core, hashing is the process of taking an input (or "message") of any length and converting it into a fixed-length string of characters. This output string is called a hash value, hash code, digest, or simply a hash. The algorithm or function that performs this transformation is called a hash function.
Think of a hash function like a highly specialized blender:
- You can put anything into it (a short text, a long document, a file).
- It always produces the same amount of "blend" (the fixed-length hash).
- If you put the exact same ingredients in again, you'll get the exact same "blend".
- If you change even one tiny ingredient, the final "blend" will look completely different.
The key is that this "blending" process is designed to be one-way. You can't take the "blend" (the hash) and figure out the original ingredients (the input data).
How Does Hashing Work? The Basic Principles
While the internal mathematics of hash functions can be very complex, the basic principles they follow are straightforward:
- Deterministic: This means that for a given input, a hash function will always produce the exact same hash output. If you hash "hello world" today, and then hash "hello world" again next year using the same algorithm, you will get the identical hash value.
- Fixed Output Size: Regardless of whether your input is a single word or an entire book, the hash output will always be the same length. For example, the SHA-256 algorithm always produces a hash that is 256 bits (or 64 hexadecimal characters) long.
- Efficiency: Hash functions are designed to be computationally efficient. Calculating a hash should be a fast process, even for large inputs.
- Pre-image Resistance (One-Way): This is a critical property. It should be computationally infeasible to reverse the process – meaning, given a hash value, it should be extremely difficult (practically impossible for secure algorithms) to figure out the original input data that produced it. This is why hashing is not encryption (which is two-way).
- Collision Resistance: It should be extremely difficult to find two different inputs that produce the exact same hash output. This is known as a "hash collision." While theoretically possible for any hash function (due to the fixed output size), a secure hash function makes the probability of finding a collision astronomically low.
- Avalanche Effect: A small change in the input data (e.g., changing a single character) should result in a drastically different hash output. This ensures that similar inputs don't produce similar hashes.
What is Hashing Used For? Common Applications
- Verifying File Integrity: When you download a file, software providers often list a hash value (e.g., SHA-256) for it. You can calculate the hash of your downloaded file using an online hash generator like ours and compare it. If the hashes match, you know the file hasn't been corrupted during download or tampered with.
- Secure Password Storage: Websites should never store your passwords in plain text. Instead, they store the hash of your password. When you log in, the site hashes the password you enter and compares it to the stored hash. If they match, you're authenticated. For this purpose, modern systems use specialized slow hashing functions like Bcrypt to make attacks even harder.
- Digital Signatures: Hashing is a key component of digital signatures. To sign a document digitally, a hash of the document is created, and then this hash is encrypted with the sender's private key. Anyone with the sender's public key can verify the signature, ensuring the document's authenticity and integrity.
- Data Structures (Hash Tables): In programming, hash tables (or hash maps) are data structures that use hashing to store and retrieve data very quickly. They are fundamental for efficient database indexing and caching.
- Blockchain Technology: Cryptocurrencies like Bitcoin rely heavily on hashing. Each block in the blockchain contains a hash of the previous block, creating a secure, tamper-proof chain. Hashing is also used in the "proof-of-work" mining process.
Hashing vs. Encryption: What's the Key Difference?
This is a very common point of confusion. While both hashing and encryption are cryptographic techniques used to transform data, they serve different purposes and work in fundamentally different ways:
| Feature | Hashing | Encryption |
|---|---|---|
| Purpose | Integrity & Verification | Confidentiality |
| Direction | One-way (cannot be reversed) | Two-way (can be decrypted) |
| Output Size | Fixed length | Variable length |
| Key Used? | No | Yes |
| Use Case | Password storage, file checksums | Secure communication, protecting data |
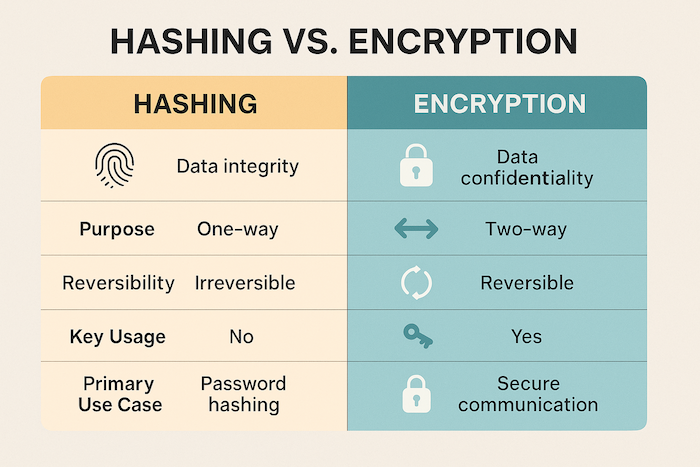
So, is hashing better than encryption? They are not better or worse; they are different tools for different jobs. You use hashing when you need to confirm data hasn't changed, and you use encryption when you need to keep data secret.